Scan Private Networks
Prerequisites
Introduction
While many certificates are publicly trusted and added to certificate transparency logs, many large organizations also manage an internal PKI that issues certificates for critical internal resources. EZMonitor enterprise plans include scanning of those networks to also monitor those certificates. In this page we will go over how to set up our scanning tool to scan your network and report the finding to your EZMonitor account.
Adding IPs and Domains to Scan
Using the Portal
- Fist, go to the EZMonitor Portal.
- Login.
- In the menu, select “Private Endpoints”.
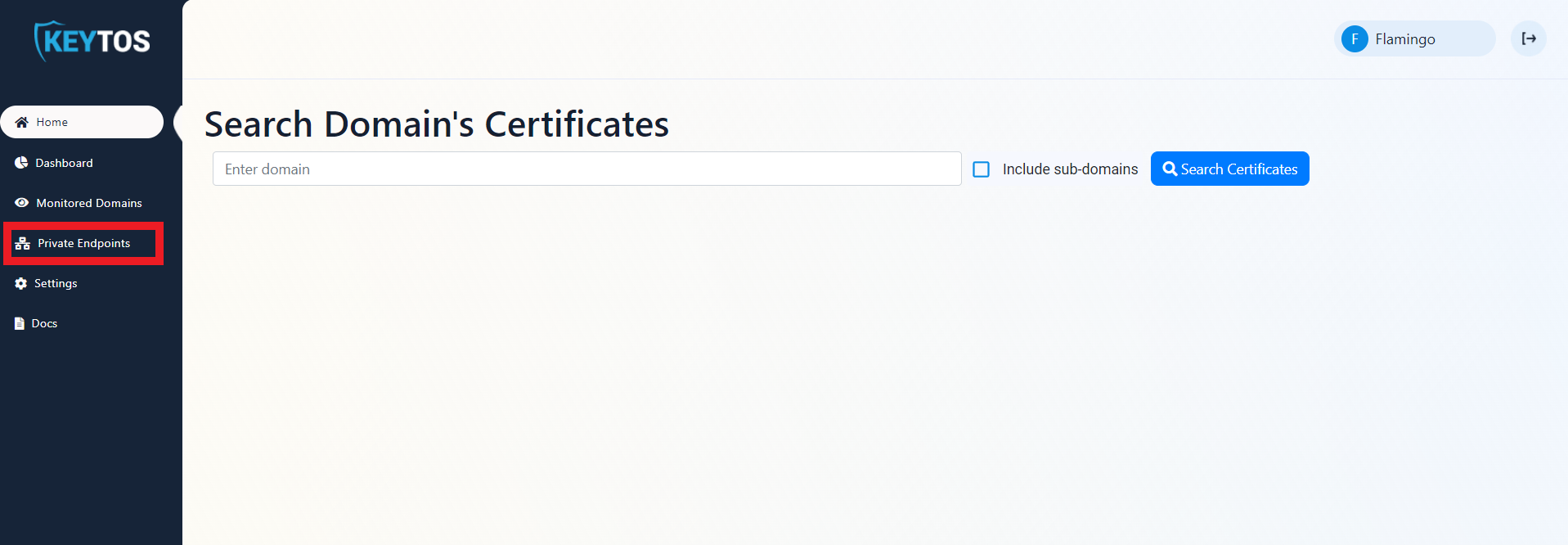
- Add the endpoints and IP addresses you want EZMonitor to monitor.
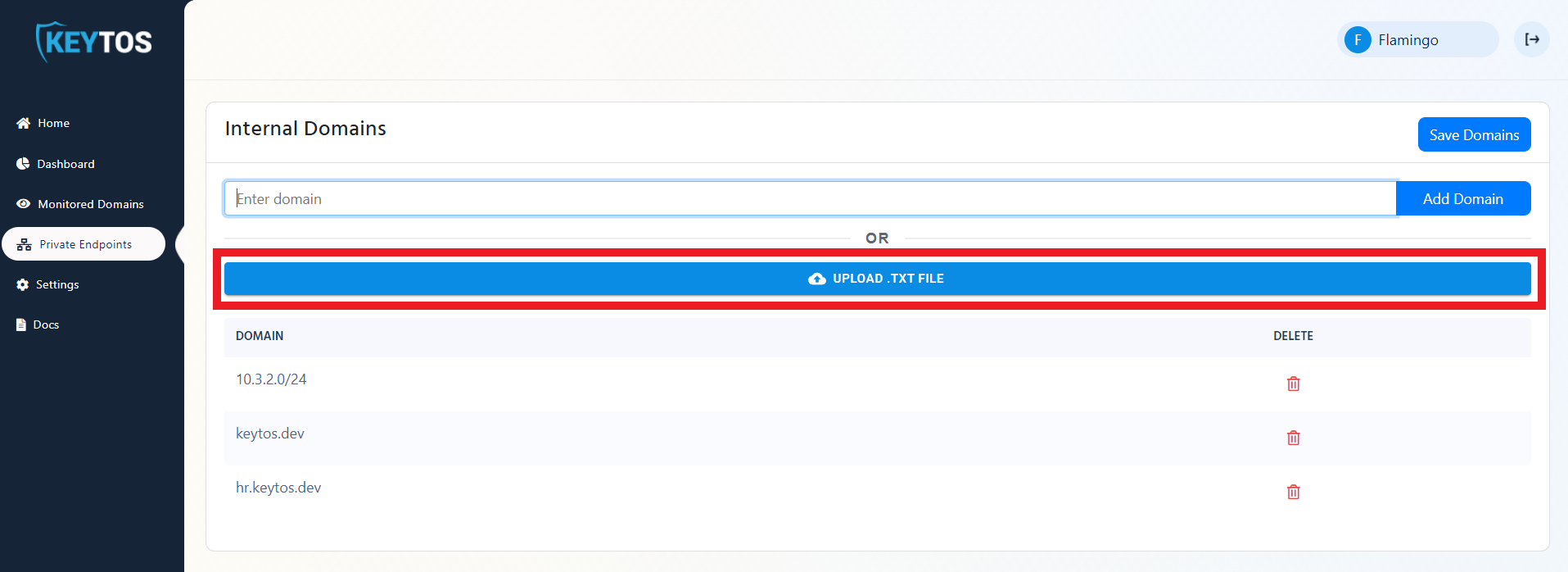
- Upload a txt file containing all the domains or IP addresses you want EZMonitor to scan.
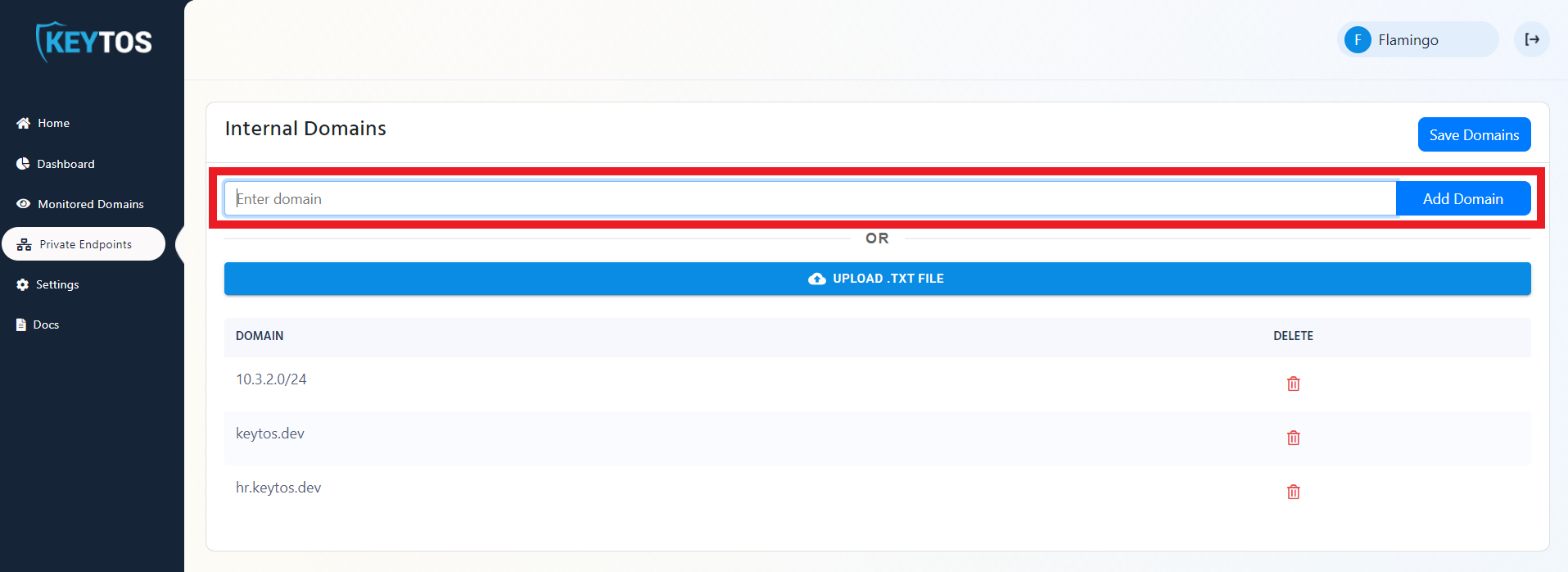
- Manually enter each domain or IP address you want EZMonitor to scan.
- Upload a txt file containing all the domains or IP addresses you want EZMonitor to scan.
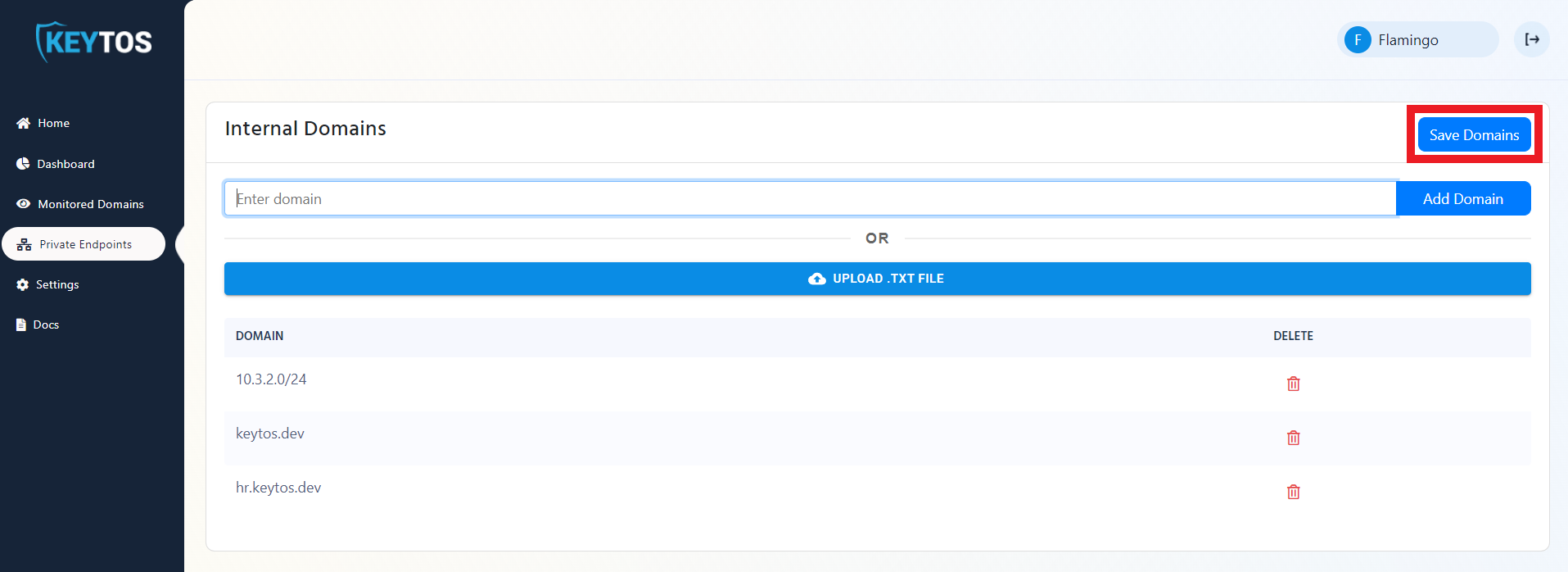
- Click Save Domains
Using EZScan
EZScan is the tool that helps EZMonitor gain visibility into your private network. To help you detect your existing certificates, EZScan has two asset detection functions:
Active Directory Certificate Services (ADCS) Certificate Download
This function contacts your ADCS Certificate Authority and downloads all the certificates issued by that CA and uploads them as certificates to track to EZMonitor.
- Download the EZScan tool to a domain joined machine.
- Run EZScan from an account (we recommend using a gMSA) that has read access to the CA’s database. With the following parameters:
- -ca and the CA name in the format: CA.HOSTNAME.DOMAIN\CA NAME
- (Optional) -t and the comma separated list of templates you want EZScan to get. If this option is not passed, all certificates will be downloaded.
- -azt your Azure tenant ID
- -sub your EZMonitor subscription ID
- (Optional) EZMonitor can use your MSI or Azure CLI token to authenticate EZMonitor. However, if you prefer using an Azure Service principal, you must pass the following parameters:
- -app the application ID of the service principal being used.
- -cert the certificate subject name used for authentication (EZScan will look in the user certificate store and get the latest certificate matching that subject name).
- (Optional) -ai an application insights key were EZScan can send run telemetry, this enables you to create alerts and detect issues with EZScan.
.\EZScan.exe -ca "CA.HOSTNAME.DOMAIN\CA NAME" -t 1.3.6.1.4.1.311.21.8.60601.4814192.14238359.2561337.13409557.15.15002822.720910 -azt YOURAZURETENANTID -sub YOUREZMONITORSUBSCRIPTIONID
Active Directory DNS Lookup
This function will query your Active Directory DNS server and will query all the DNS entries registered in the domain and will add them as private domains in EZMonitor.
- Download the EZScan tool to a domain joined machine.
- Run EZScan from an account (we recommend using a gMSA) that has read access to the to the DNS entries. With the following parameters:
- -dns this is the hostname of your DNS Server: HOSTNAME
- -domain the domain (DNS Zone) you want EZScan to scan.
- -azt your Azure tenant ID
- -sub your EZMonitor subscription ID
- (Optional) EZMonitor can use your MSI or Azure CLI token to authenticate EZMonitor. However, if you prefer using an Azure Service principal, you must pass the following parameters:
- -app the application ID of the service principal being used.
- -cert the certificate subject name used for authentication (EZScan will look in the user certificate store and get the latest certificate matching that subject name).
- (Optional) -ai an application insights key were EZScan can send run telemetry, this enables you to create alerts and detect issues with EZScan.
.\EZScan.exe -dns HOSTNAME -domain YOURDOMAIN -azt YOURAZURETENANTID -sub YOUREZMONITORSUBSCRIPTIONID
Scanning The Network
To scan the network to detect detect SSL certificate problems, EZScan will download the list of domains and IP addresses gathered in the previous steps and will scan each one of them and will record the SSL status of the endpoint. To start the scan, run EZScan with the following parameters:
- -azt your Azure tenant ID
- -sub your EZMonitor subscription ID
- (Optional) -p Ports to scan, by default EZscan will scan port 443 and 80, if you want to scan a custom port range, enter the port numbers in a comma separated list.
- (Optional) EZMonitor can use your MSI or Azure CLI token to authenticate EZMonitor. However, if you prefer using an Azure Service principal, you must pass the following parameters:
- -app the application ID of the service principal being used.
- -cert the certificate subject name used for authentication (EZScan will look in the user certificate store and get the latest certificate matching that subject name).
- (Optional) -ai an application insights key were EZScan can send run telemetry, this enables you to create alerts and detect issues with EZScan.
.\EZScan.exe -azt YOURAZURETENANTID -sub YOUREZMONITORSUBSCRIPTIONID