3. Connecting to SIEM
Prerequisites
Introduction
EZMonitor enables your security team to monitor critical information with: intuitive dashboards, email alerts, as well as pushing the information to your SIEM.
If your SIEM provider is not currently supported email your Keytos contact and request a connector for that specific provider.
Connecting To Azure Sentinel
- Go to the EZMonitor Portal.
- Login.
- Click on Settings.
- Expand your subscription’s advanced settings.
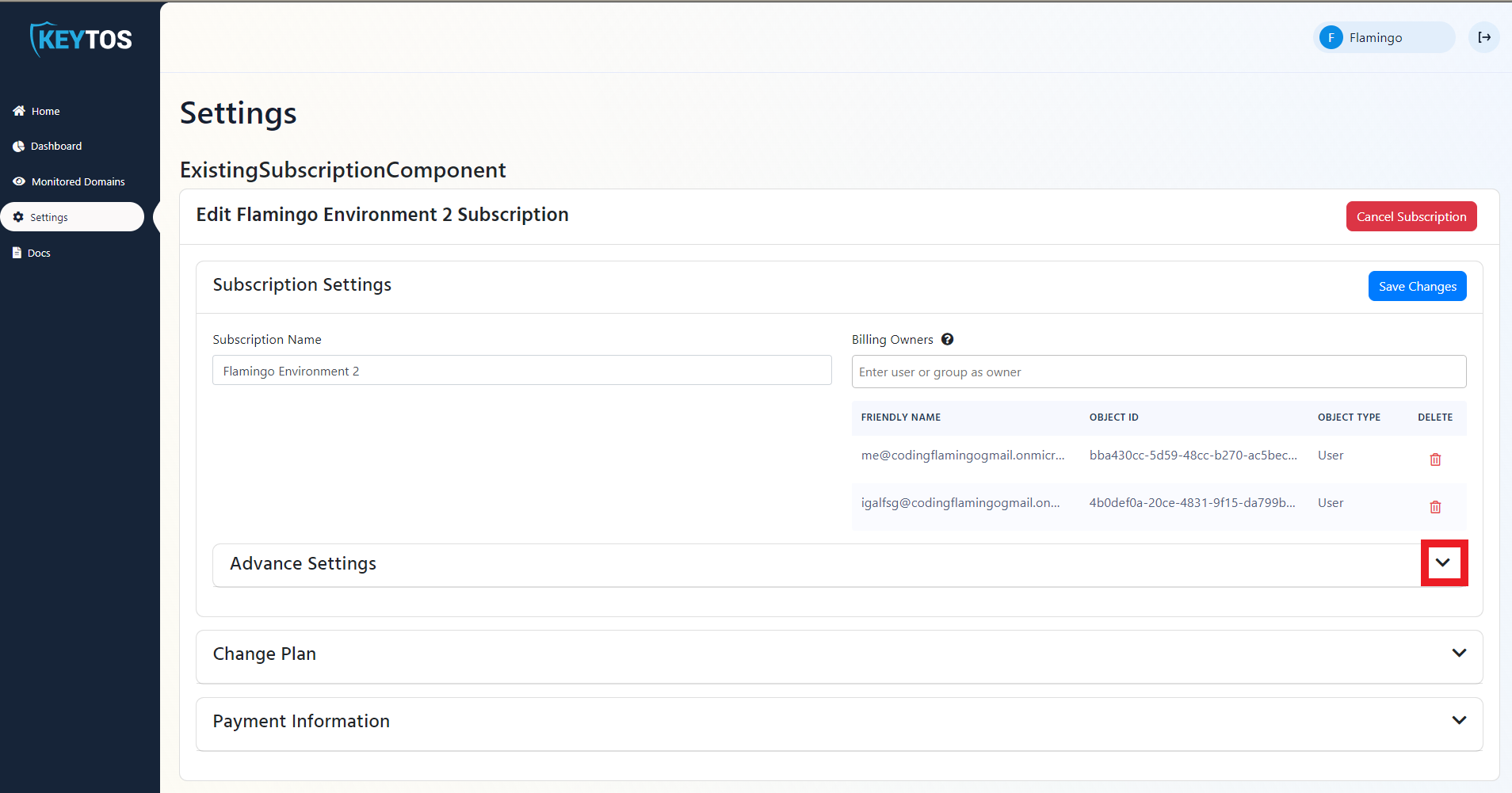
- Enable the “Send Alerts to SIEM” option.
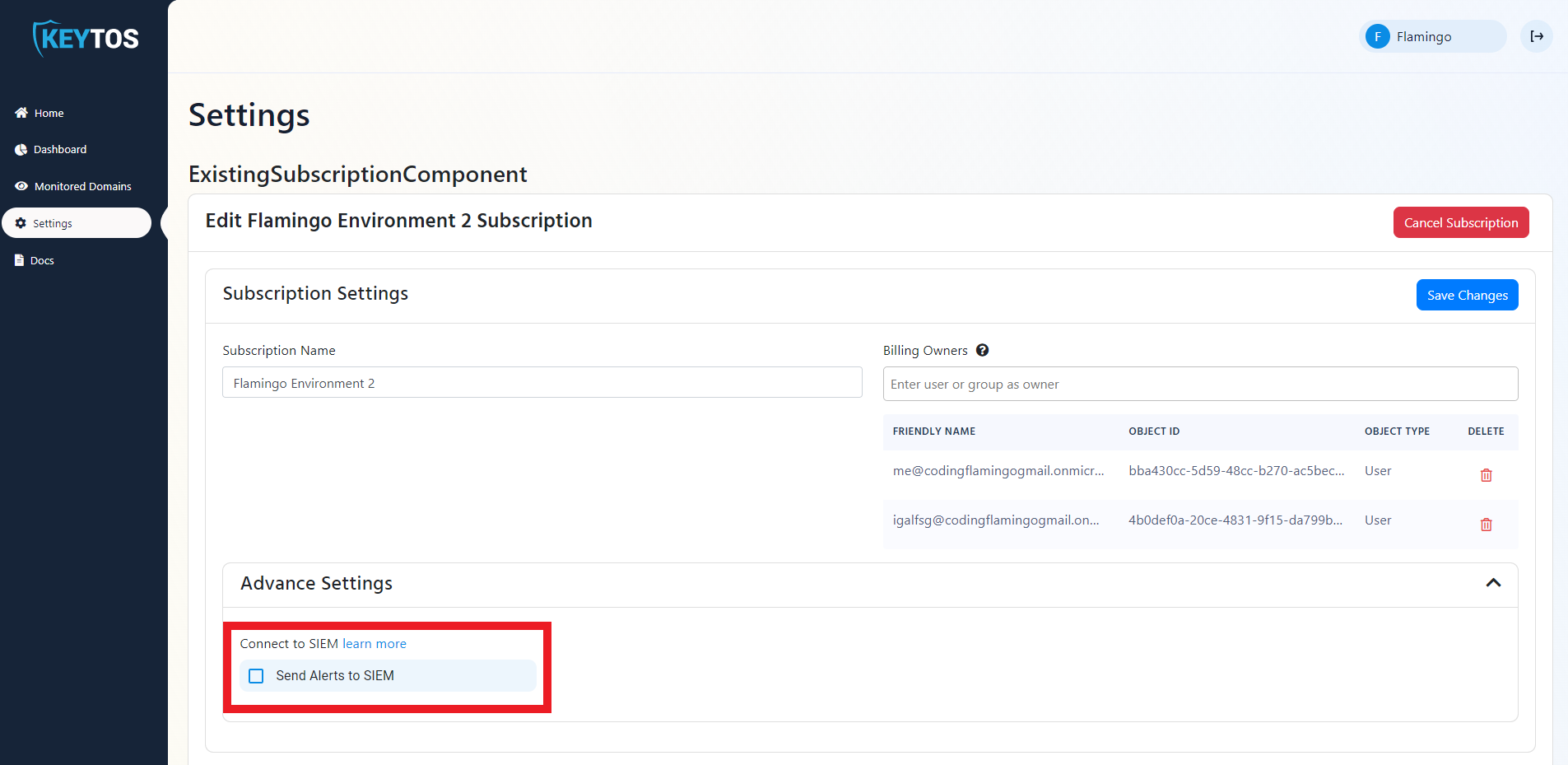
- Select Sentinel as the SIEM Provider.
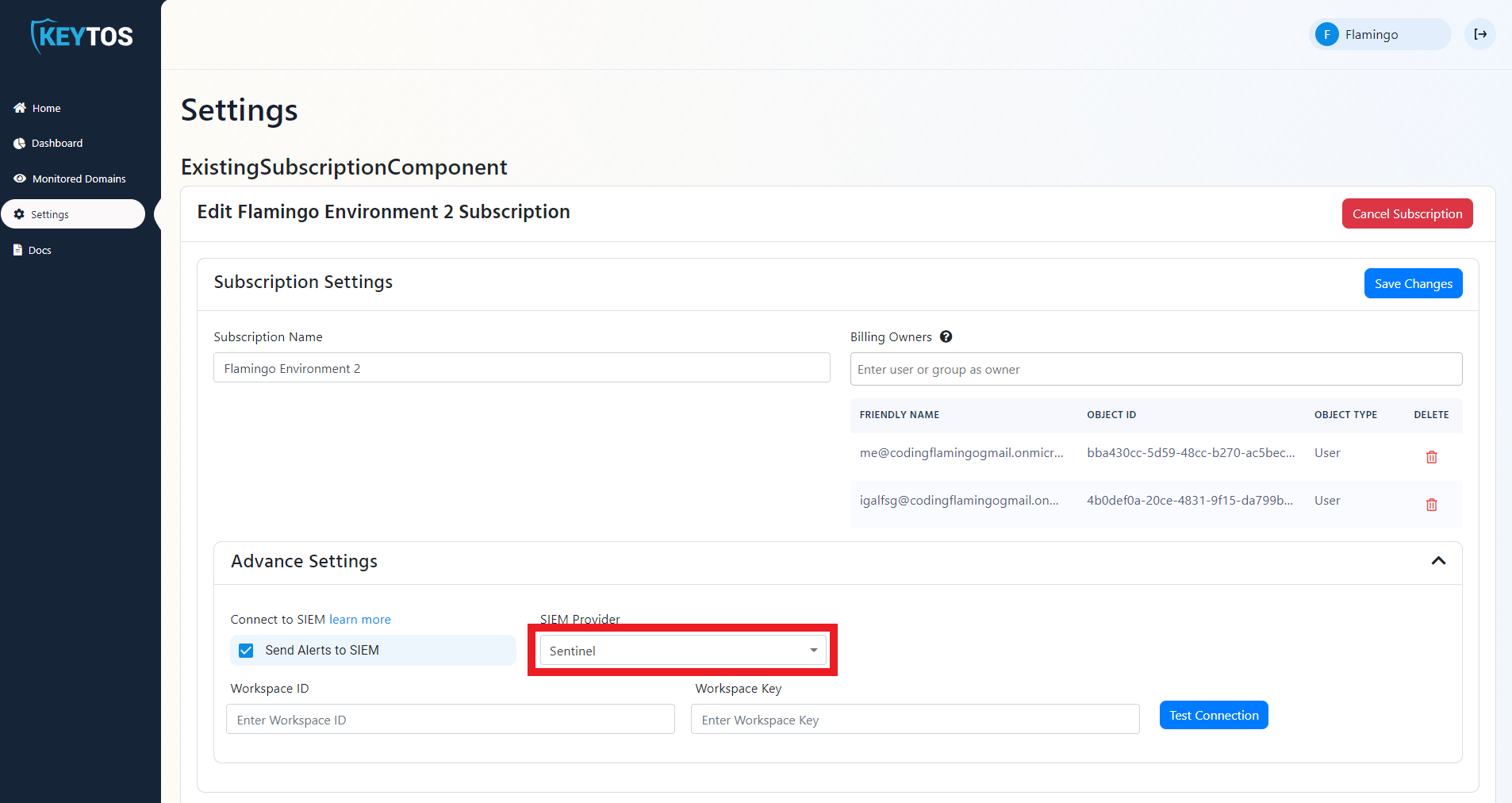
- In another tab, go to the Azure Portal
- Select the log analytics connected to your Sentinel instance.
- Click on “Agents Management”.
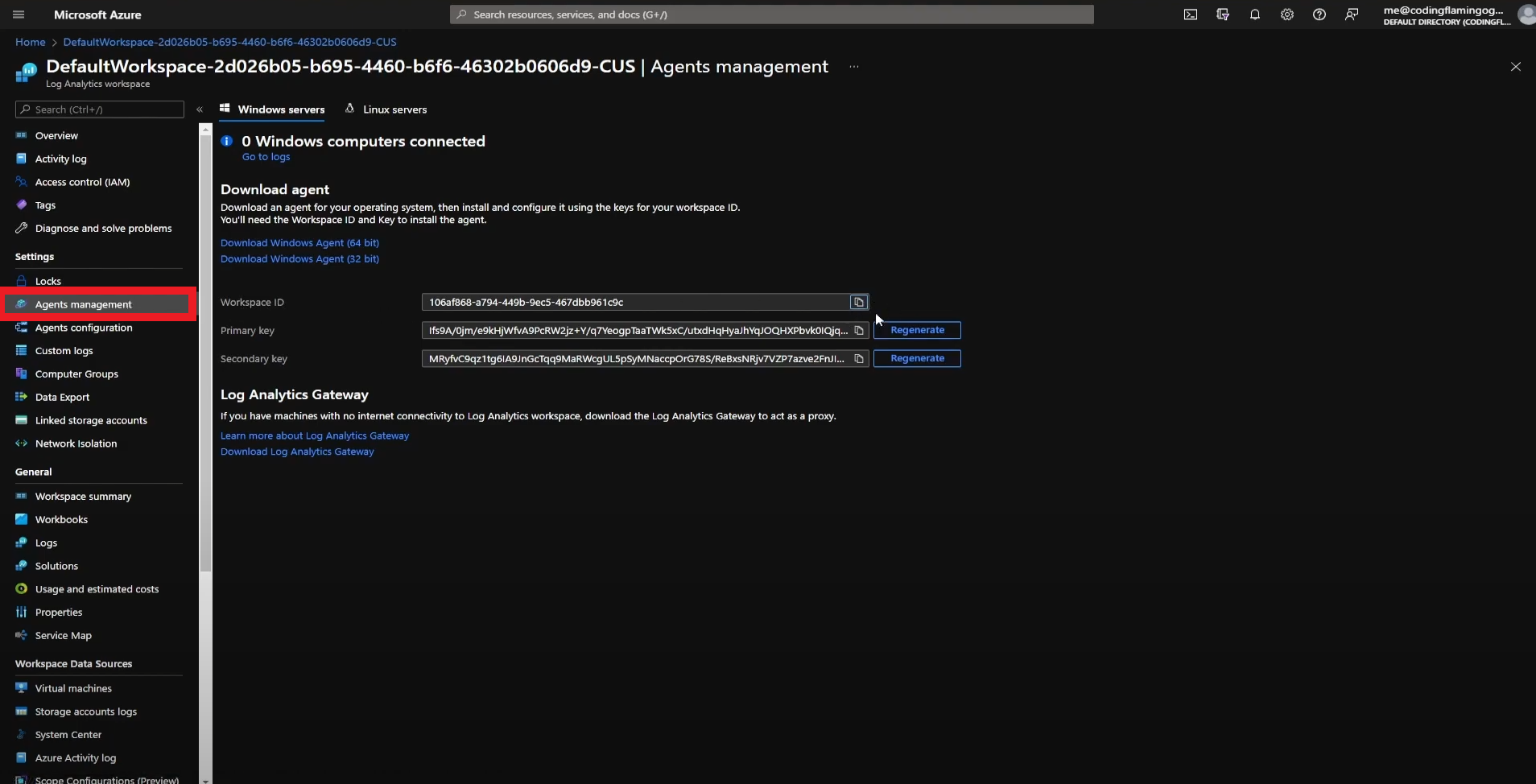
- Copy Your Workspace ID.
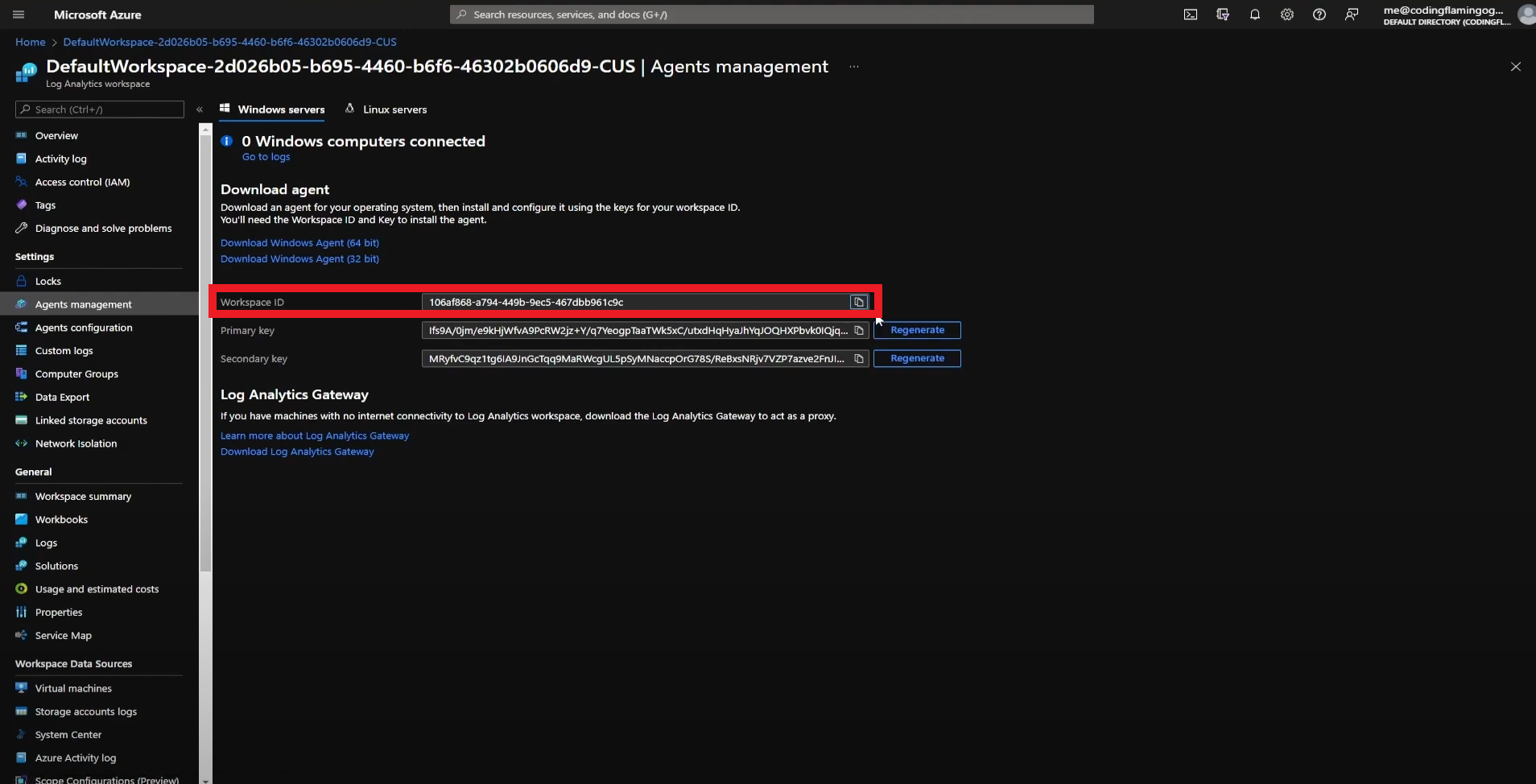
- Go back to the EZMonitor tab and paste it in the “Workspace ID” field.
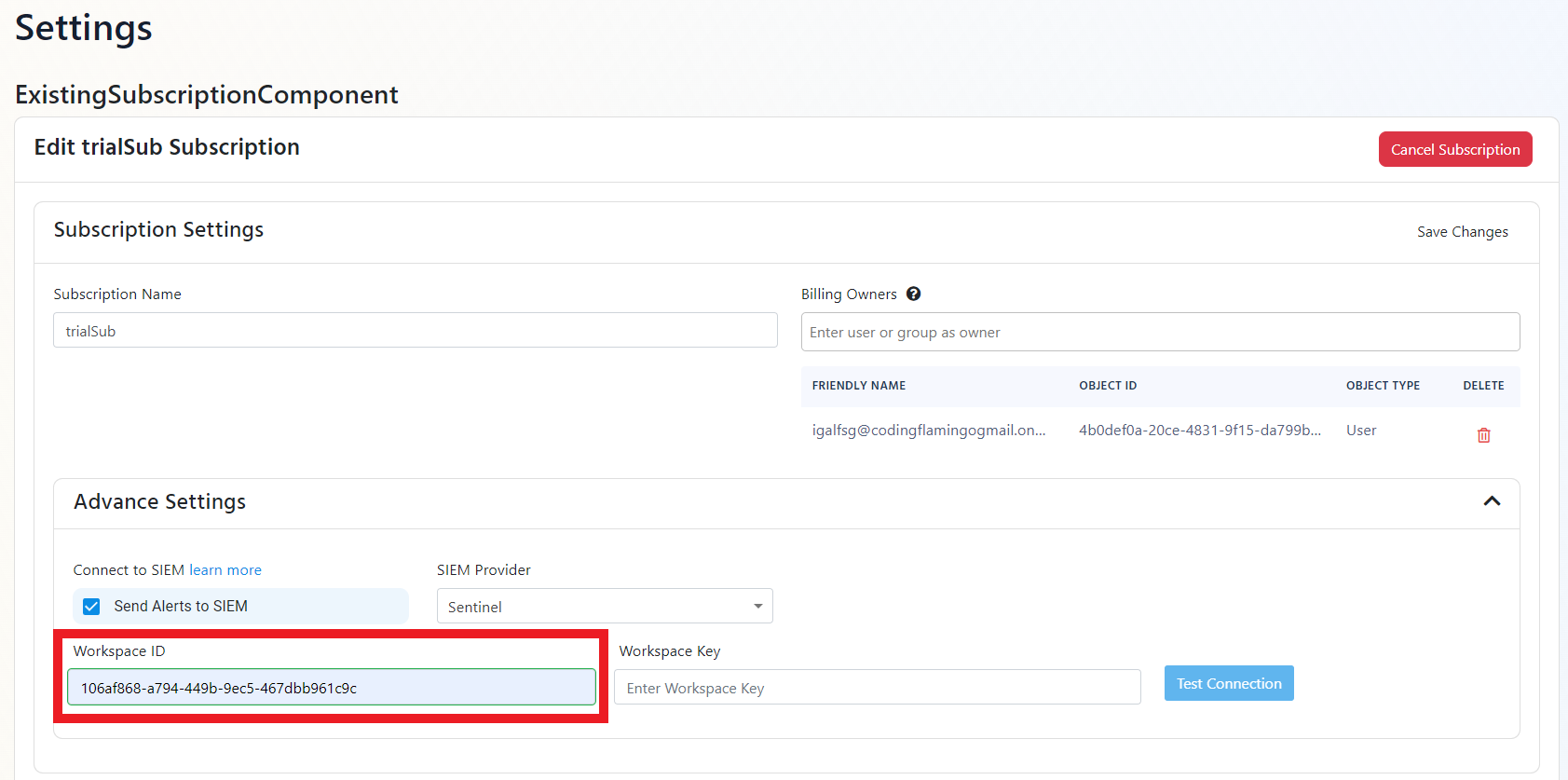
- Go back to the Azure tab and copy the primary key.
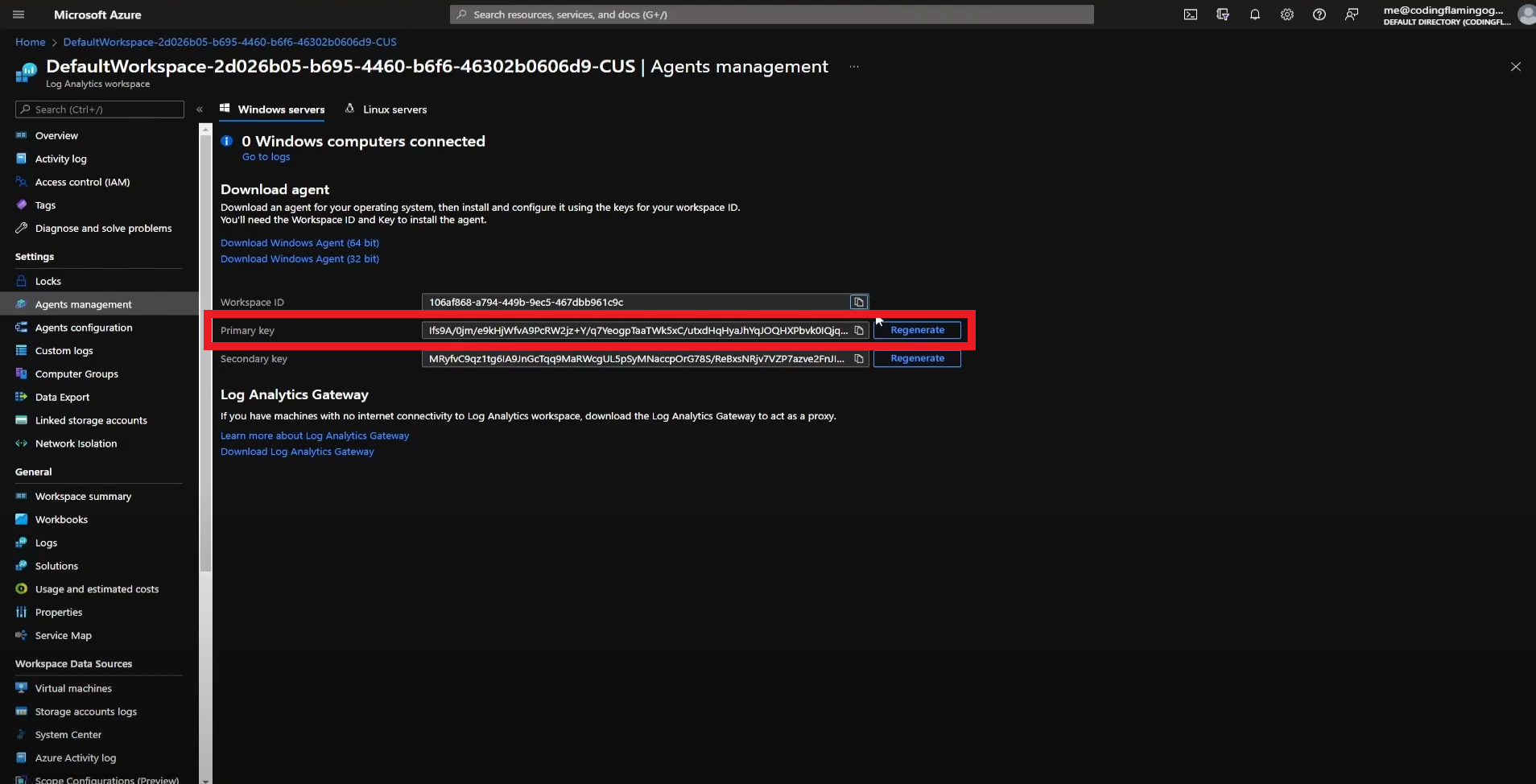
- Go back to the EZMonitor tab and paste the key in the “Workspace Key” field.
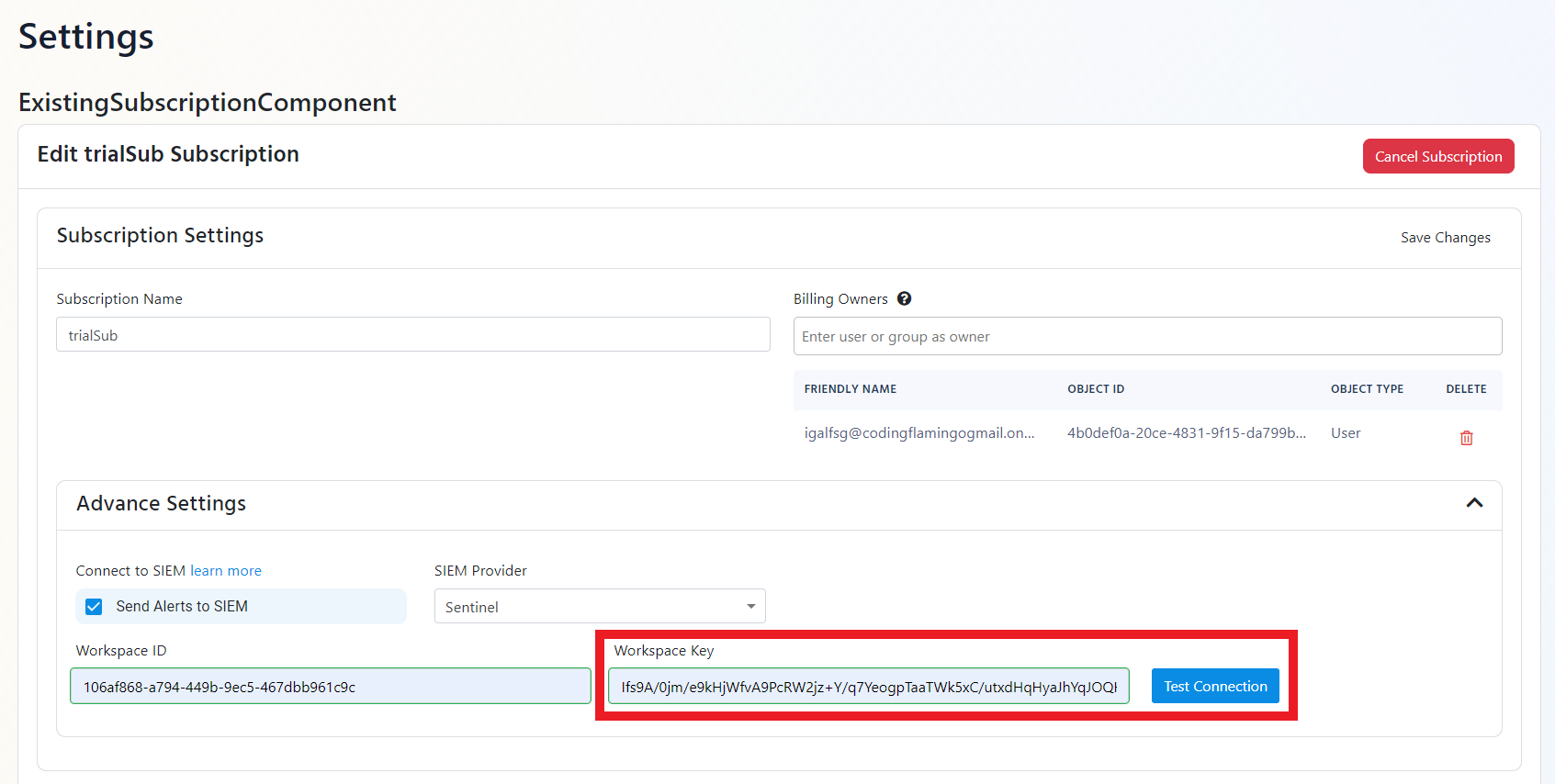
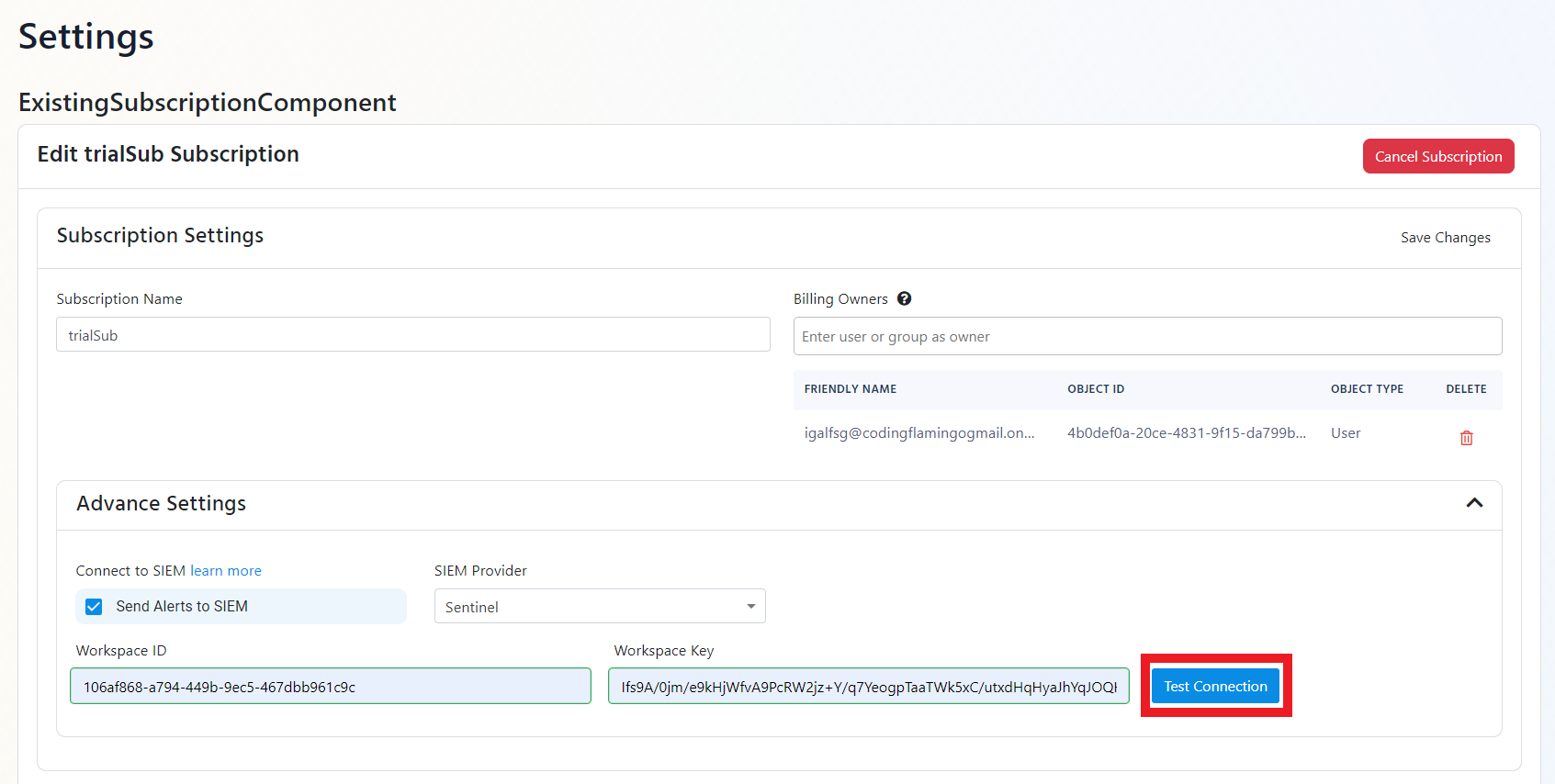
- Click the “Test Connection” button, this will create a test log in your SIEM to make sure EZMonitor can write to the EZMonitor.
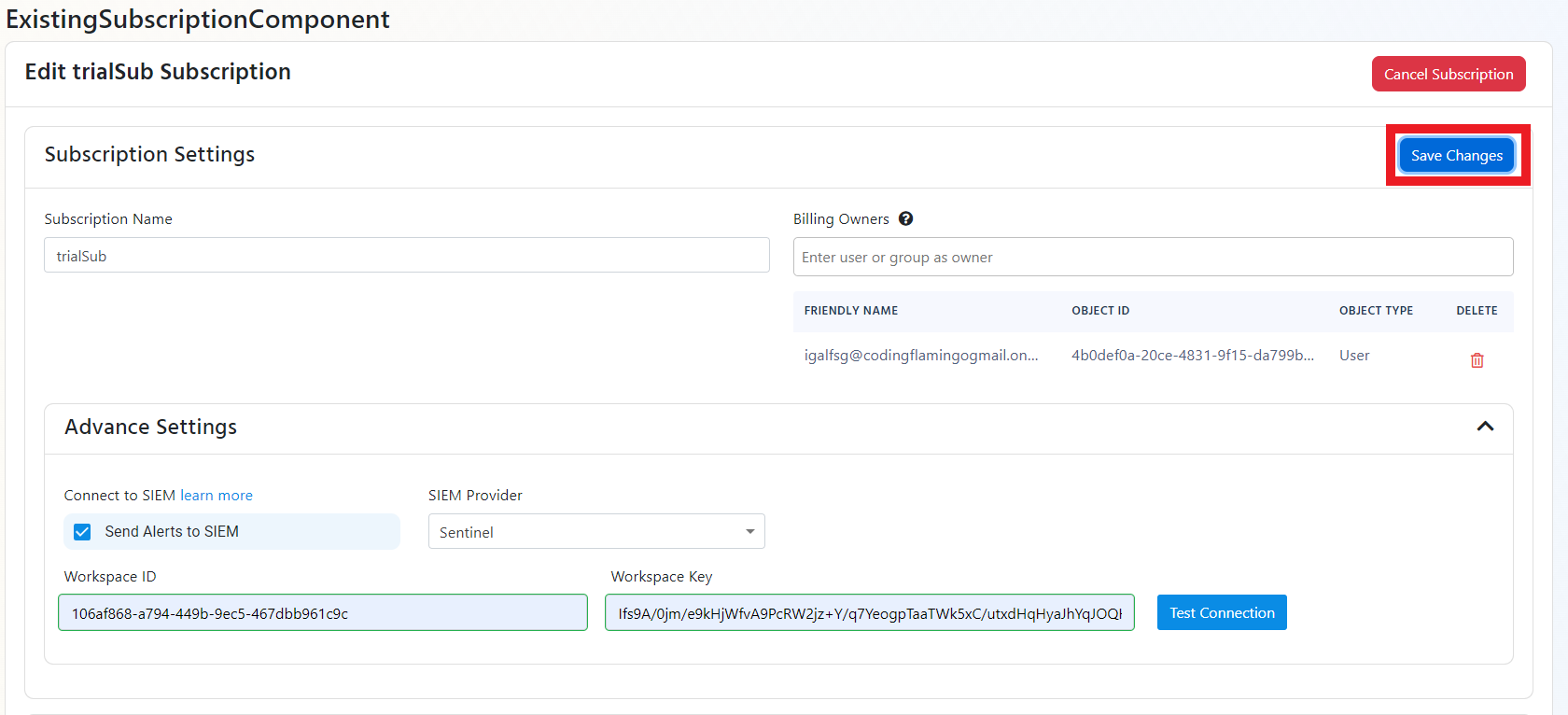
- If the connection test is successful, click “Save changes”.
- EZMonitor will now send your security alerts to your SIEM. If an error occurs it will email your subscription administrators. See below to see the different events EZMonitor will send
SIEM Events
Below is the list of events EZMonitor and their corresponding Event ID. Use this information to create custom alert rules and automation to mitigate the issues.
EZ Monitor Events
EZMonitor has two types of alerts, The first type are alerts generated by scanning Certificate Transparency logs, and the second are alerts generated by scanning the SSL health of your servers.
Certificate Transparency Logs Based Alerts
| Event ID | Event Summary | Description |
|---|---|---|
| 12 | A similar domain has been found. | A domain that might be impersonating your domain was found please verify this domain is not being used to impersonate your organization. |
| 18 | Your domain is vulnerable to domain takeover. | Your DNS record is pointing to an Azure resource that is no longer being used. please remove the CNAME record pointing to this resource to avoid a bad actor taking over your sub domain. |
| 20 | A certificate was issued from a different Root CA. | A certificate was issued from a different Root CA, verify with your team to make sure this certificate was issued by someone in your organization. |
| 25 | A new sub domain was registered. | A new sub domain found, please verify with that this action was done by someone in your organization. |
| 29 | CAA Mismatch. | A certificate was issued by a CA not allowed by your CAA policy. |
Network Scan Based Alerts
| Event ID | Event Summary | Description |
|---|---|---|
| 19 | The newest certificate is not installed in your server. | A certificate that is expiring soon has been renewed, but our systems detect that it has not been installed in all your web servers. |
| 26 | No subject alternative name matches the domain. | The certificate returned by the server does not have any subject names matching the domain, this can cause an error when the user is accessing the site. |
| 27 | The server did not serve a certificate when an HTTP request was sent | The server did not return a certificate. Please make sure HTTPS is enabled and the server has a valid certificate and the certificate is binded to this domain. |
| 28 | Certificate contains wild-card Subject Alternate Name | This Certificate contains a wild card subject alternate name. This type of subject alternate name can cause an outage since there is not record of where this certificate is being used. Please change this certificate to one containing the specific domains. |
| 40 | Error validating installed certificate. | The certificate served by the server was not valid. Please check the alert details on the steps needed to solve this issue. |
| 41 | Error validating installed certificate chain. | There was a problem validating the certificate chain of the certificate served by the server. Please follow the steps on the alert to remediate this issue. |
| 42 | HTTPS Is Not Enforced | Strict-Transport-Security header was not found. Please add this header to enforce HTTPS and prevent man in the middle attacks. |
| 68 | The certificate installed in the web server is expiring soon. | The certificate installed in the web server is expiring soon. Please install the latest certificate to avoid an outage |
| 99 | Certificate is expiring soon. | Your domain’s certificate is expiring soon, and it has not been renewed. Renew your certificate and replace the expiring certificate to avoid an outage |
Internal Network Scan Based Alerts (Includes all Network Scan Alerts)
| Event ID | Event Summary | Description |
|---|---|---|
| 30 | This Certificate Has Been Revoked | This Certificate has been revoked and will rejected by clients. Please create a new certificate and install it in this endpoint. |
| 31 | Self Signed Certificate | This Certificate is self signed, please issue a certificate from a trusted authority. |
| 32 | The CRL was not accessible when EZMonitor tried downloading it | EZMonitor was not able to download the CRL, make sure your CRL is available in your network |
| 33 | SHA1 Certificate | This certificate uses SHA1 hashing algorithm. This algorithm is no longer secure, please replace this certificate with a certificate using a stronger hashing algorithm. |
| 34 | Weak Cryptographic Key | This certificate uses a weak cryptographic algorithm. Please replace this certificate with a certificate using a stronger cryptographic key. |
| 35 | Current CRL is expired | EZMonitor downloaded an expired CRL, make sure your CRL is updated in all your CRL endpoints. |
Creating Alerts in Azure Sentinel
Using Azure Sentinel enables you to create alerts and automation for critical operations or abnormal behavior. We recommend setting up alerts for all EZMonitor events. Below are sample queries that can be used to create alerts. The best way to separate each alert is by their Vulnerability ID, below is a query that will return all the dangle DNS entries that are vulnerable to domain takeover.
EZMonitor_Alerts_CL | where VulnerabilityID_d == 18