Create CAA Record
Prerequisites
What are CAA Records
A Certification Authority Authorization (CAA) record is a DNS entry type that enable to limit which Certificate Authorities (CAs) are allowed to create certificates for your domain. Compliant Certificate Authorities must check if they are allowed to issue a certificate for your domain, and notify your contact if someone requests a certificate from an unauthorized CA.
If a CAA is present, only certificates from the listed CAs are allowed. However, CAA records fail open meaning that if no CAA record is present any CA can create certificates for the domain.
Creating CAA Records
The CAA record is a DNS entry of the with the following format:
CAA <TTL> <Tag> <Value>
TTL (Time to live) is how long should the resolver should keep the DNS entry. For CAA Entries the standard TTL is 0 seconds, ensuring the CA gets the latests restrictions with each request.
Tag The tag is what type of CAA entry it is. There are 3 types of CAA Entries: 1. issue Authorizes a specific CA to issue certificates for this domain. 1. issuewild Authorizes a specific CA to issue wildcard certificates for this domain. 1. iodef Contains the email that should be contacted if a request is made to an unauthorized CA.
Sample CAA
If more than one CA is used by a domain each CA must have its own entry. Below is the keytos.io CAA entries:
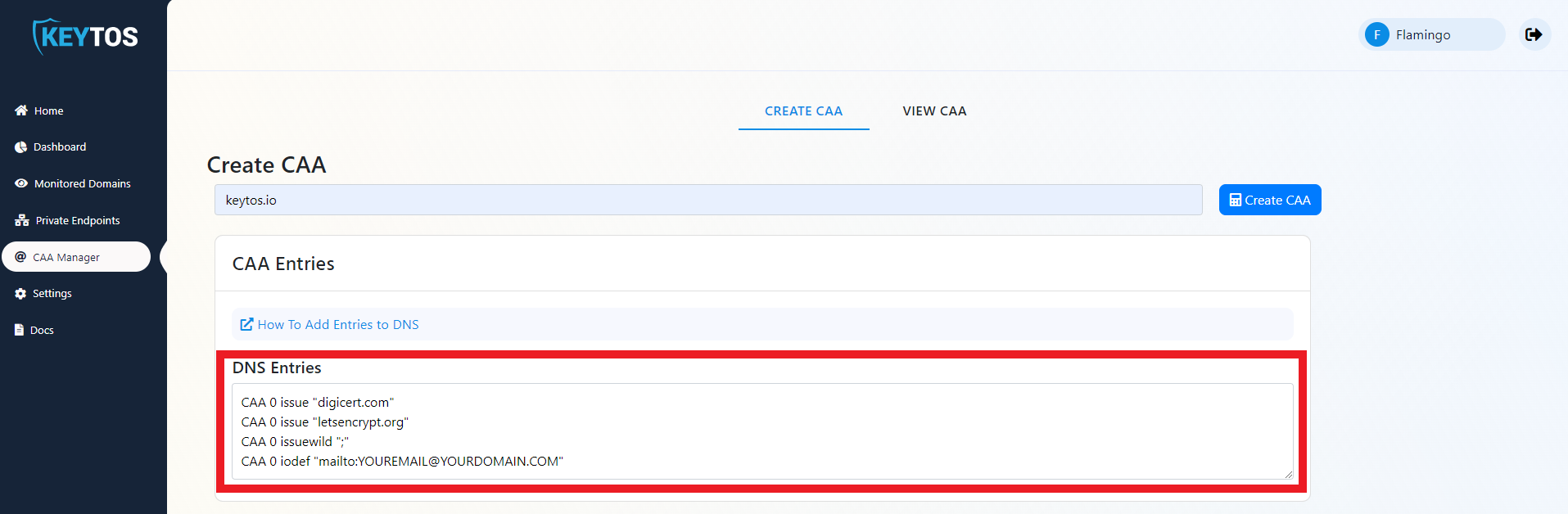
keytos.io CAA 0 issue "letsencrypt.org"
keytos.io CAA 0 issue "digicert.com"
keytos.io CAA 0 issuewild ";" //block all wildcard certificates
keytos.io CAA 0 iodef "security@keytos.io"
Using the Portal
Setting up CAA records is a simple action. However, it requires a lot of planing to ensure all CAs used by the domain are added to the policy, since missing a Certificate authority can cause an expensive outage.
Since EZMonitor monitors all certificates issued around the world, we can help you identify the CAs used by your organization and create your CAA policy in minutes.
Create CAA Records
- Fist, go to the EZMonitor Portal.
- Login.
- In the menu, select “CAA Manager”.
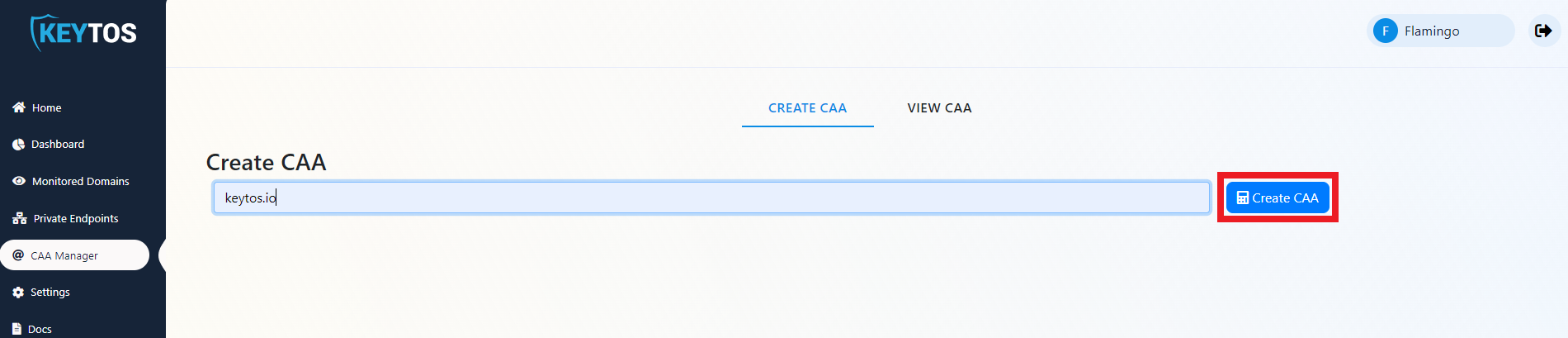
- Enter your domain.
- Click “Create CAA”.
- Analyze the returned policy and ensure it is on par with your security policy of allowed CAs.
- Login into your DNS provider.
- Enter each CAA record for your domain.
Change the iodef entry to a share mailbox that is monitored by your security team.
Validate CAA Records
- Fist, go to the EZMonitor Portal.
- Login.
- In the menu, select “CAA Manager”.

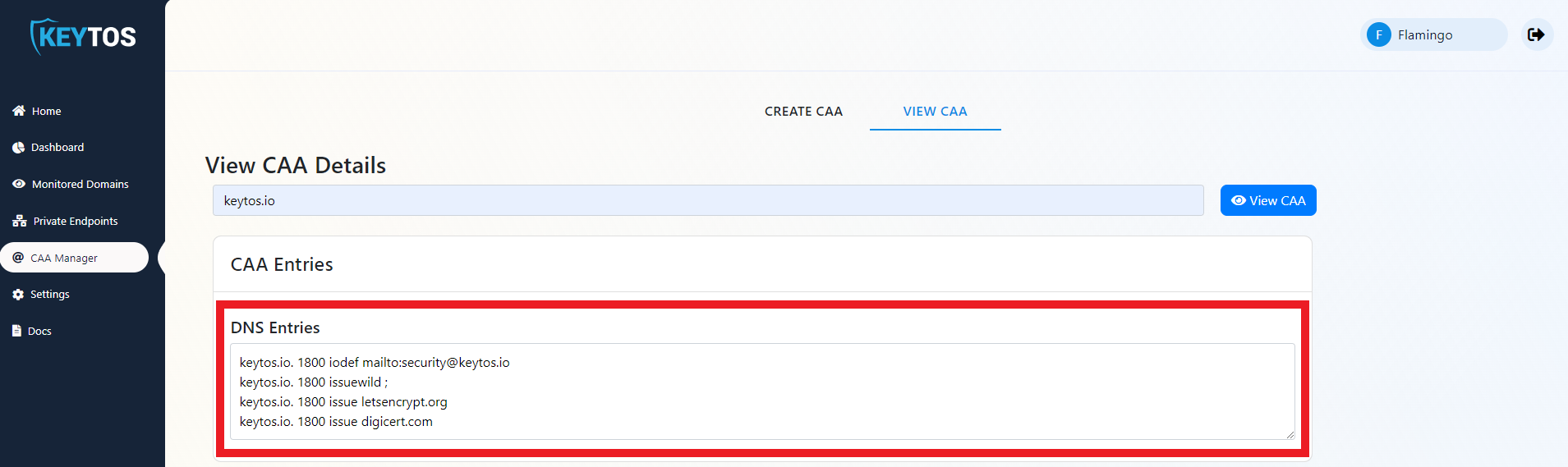
- Select the View CAA Tab
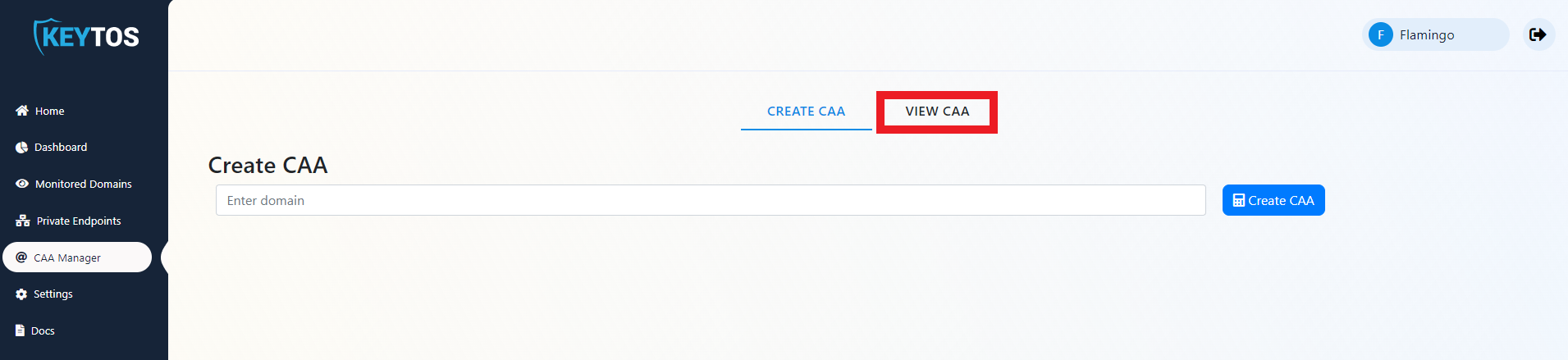
- Enter your domain.
- Click “View CAA”.
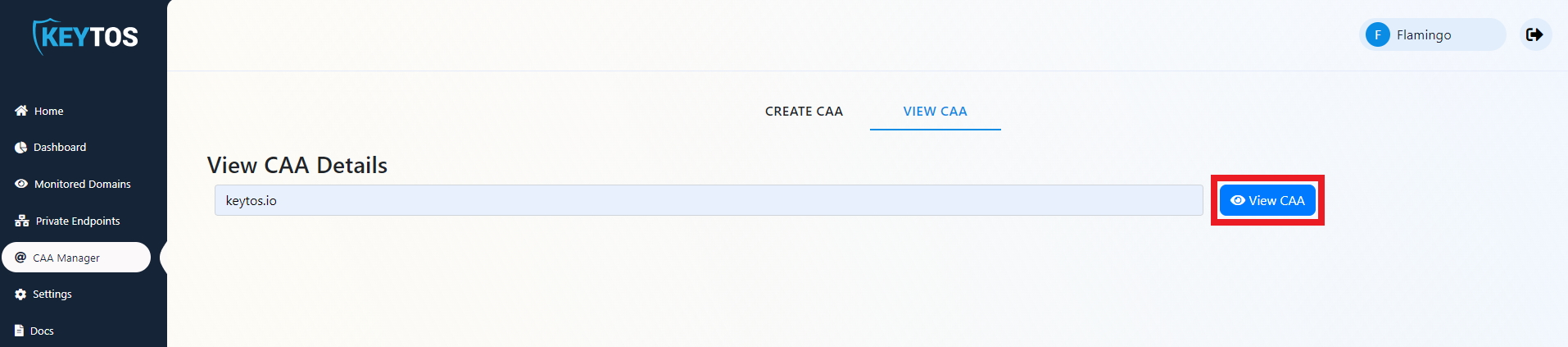
- Analyze the returned policy and ensure it is on par with your security policy of allowed CAs.